PDPA Compliance Solution
PDPA āļāļ·āļāļāļ°āđāļĢ
Personal Data Protection Act – and What It Means for Business
As we known, the National Legislative Assembly approved the Personal Data Protection Act (“PDPA”). The Act is aimed at regulating the lawful collection, use or disclosure of personal data that can directly or indirectly identify a natural person. The PDPA is designed to protect a data owner from the unauthorised or unlawful collection, use or disclosure and processing of their personal data.
PDPA Data classification levels
Top Secret is if revealed There will be the most serious damage to the security and sovereignty of a country. National order and state interests Including international relations
Secret means the case is disclosed. There will be serious damage to the administration of State affairs. Administration of justice Development of national infrastructure Public health system Information technology, innovation, etc.
Confidential means that If it is opened there will be damage to human rights. And the performance of duties of government officials, etc.
Personal information means information about an identified individual that can directly or indirectly identify a natural person such as Citizen id, Date of birth, Religion, Salary, etc.
![Pyramid Chart [Recovered].jpg](/application/files/7116/4844/1722/Pyramid_Chart_Recovered.jpg)
 |
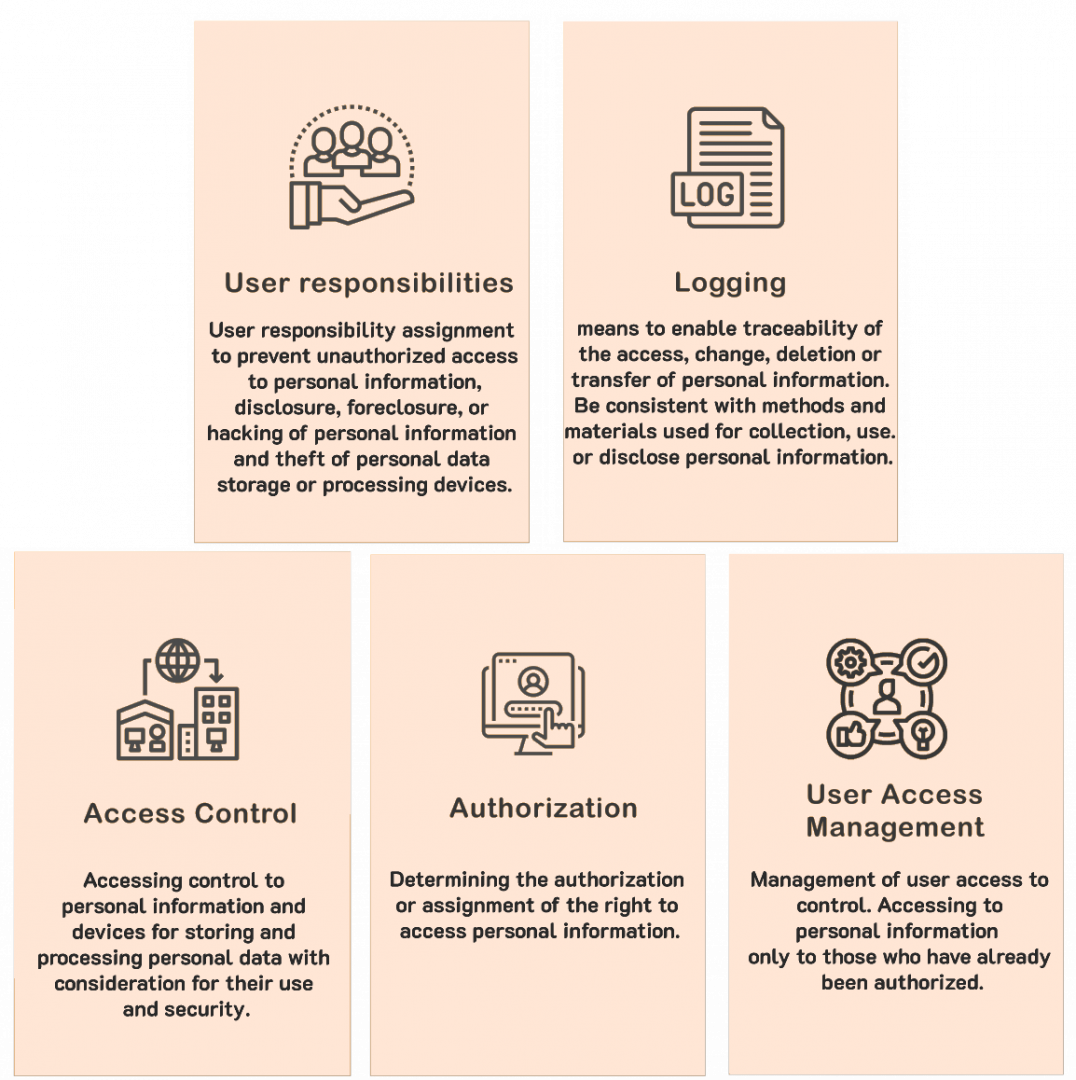
Data Discovery
A tool for searching for information of interest such as name, surname, address, telephone number, e-mail address, date of birth, ID card number. credit card number or other personal information. Stored in various formats, including Files Database Email and Cloud, this tool searches and reports the search results in the form of storage location. What type of data is it? Discovered under what conditions? |
Data ClassificationTools for classifying data, order of confidentiality or type of use such as personal information, general, secret, top secret, which the system can help determine the type of information according to the content of the information or users can easily define. |
|
 |
Data Loss PreventionA tool for detecting attempts to send data to the outside in the form of various file types. The set conditions on the system to alert or stop the operation. To prevent data leakage, for example, when a file is classified as private or confidential, its contents cannot be copied from the file. Can't send email or can't copy to flash drive |
|
Data Encryption
Tools to help encrypt various types of data such as Files, Database, Cloud, Hypervisor, etc. to prevent unauthorized access to the data. If there is someone who does not want to be able to espionate the information. It will not work because the data to use it must always be decrypted before use. |
 |
 |
Key Management
Secret key management system, according to encryption requires a secret key to encrypt the data. This can be done in a normal way that is handled by a moderator. However, if encryption is used in multiple systems, it is necessary to have a separate secret key in each system. and has a clearly defined service life This will be a problem for administrators to take care of. This system will help automatically perform functions such as set period of use and change the secret key automatically. |
Hardware Security Module
Device for storing secret keys, according to secret key is the heart of encryption. Therefore, the secret key must be assigned permissions and have a safe storage. The device is protected against physical access, for example if someone is trying to break in the device. The system destroys the secret key immediately to prevent unauthorized access. |
|
 |
Data Tokenization
The system generates a virtual dataset that is encrypted at random. To use in place of information that requires high security and avoid directly exchanging such information, such as credit card numbers. ID card number When exchanged, random values ââwill be sent out to store in the database. And to use the data, this random value must be exchanged for the original data back. Thus, this system prevents database administrators or unauthorized persons from seeing the real data. |
Data Masking
The system conceals some important information. For example, the call center staff must be able to see certain numbers to verify the identity of the contact, such as a phone number in the format 08X-XXX-4938 in order to prevent the Call Center staff from taking advantage of the information on their duties. |
 |
 |
Consent Management
Consent Management System that will be a digital consent request that will be able to work with websites and applications or adding data to the system by hand with the ability to search and store it in a database format, such as the name of the consent message consent date Consent version as well as displaying a Dashboard that shows an overview of the data. |
Cookies ConsentData management system consent to the use of cookies This is because the website uses cookies for authentication. Temporary storage Or analyzing information in various fields. This system will be able to create forms to use on the website to request consent for the use of cookies for each use. And it is stored as a consent history of each cookie ID. |
 |
 |
Data Subject Request
The system requests for personal data subjects. It is a channel used to request, correct or delete personal information. The system will look like a Web Portal that allows the data owner to create requests. Contact the data administrator and track the status through the Web Portal |
Incident ManagementIncident management system, It will be a tool that will help in supporting the implementation of the Workflow, SLA, Agent that will make the request management service. Event Status Tracking Request for approval of operations that are Automate Process for all work systems. |
|
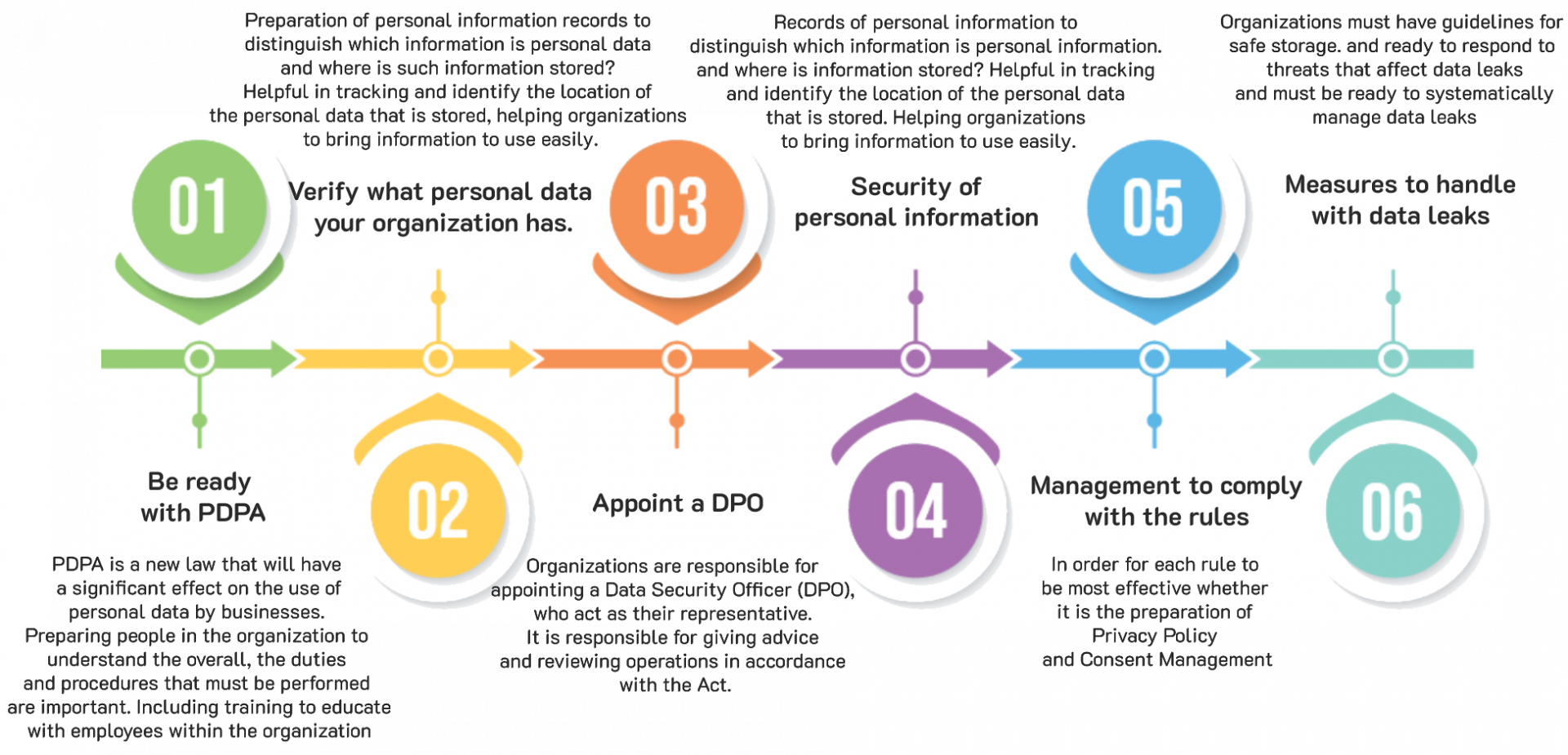
Setting up a request for receiving a consent to collect, use and transmit users’ personal data may at first seem like a task that can be completed in a short amount of time. Yet these steps are carefully regulated under the PDPA in order to ensure that user data is safeguarded in exactly the ways that the new law intends. So, Digitech one provide consulting and all solutions such as data loss prevention, cookies consent and data security. We will design best flexible solution for your business including the suitable software and effective hardware.
Consulting Service
Our team had 20 years of experience in Cybersecurity and Data Protection and guranteed by certifications. We will give you a suggestion that is designed for only your business. It will solve the problem on the right spot and more effective.
|
|
|
 |
 |
 |
 |
Contact our expert
By submitting, I agree to the processing and international transfer of my personal data by DataOne Asia as described in the Private Policy.





